
IoT Raspberry Pi SSH Remote Access over Starlink, 3G, 4G LTE, or 5G cellular network SocketXP
Setting Up SSH on IoT Devices. Before you can remotely access your IoT devices, you need to set up SSH. This typically involves installing an SSH server on the device and configuring it for secure access. Installing an SSH Server. Most Linux-based IoT devices come with an SSH server pre-installed.
Best free ssh client to use for aws linux monomouse
Best Practices for SSH-Driven IoT Remote Access. SSH tunneling is the primary method for users to securely communicate with remote servers, networks, and devices through established firewalls and gateway routers using an assigned, protected port. It allows internet traffic to travel between local and remote devices.

10 Most Popular IoT Devices That Really Work Well In 2020 FROMDEV
The command typically follows this pattern: ssh [username]@[ip address] Replace [username] with the username for the IoT device and [ip address] with the IP address of the IoT device. Authenticate: Depending on your SSH configuration, you will need to authenticate using either a password or an SSH key.
11 Of The Best SSH Client For Windows 10 To Download 🤴
Yes, SSH is a secure protocol that encrypts the connection between your computer and the IoT device. Can I use SSH to access multiple IoT devices? Yes, you can use SSH to access as many IoT devices as you need, as long as each device has SSH enabled and you know their IP addresses and login credentials. Summary. Enable SSH on the IoT device.
10 Best IoT Platforms for 2021 CyberVision Enterprise Software Development, Big Data
To ensure secure remote access for IoT devices, the most used protocols are Secure Shell (SSH), Virtual Private Networks (VPN), and Remote Desktop Protocol (RDP). These technologies offer a safe way to connect remotely and enable management of IoT systems. What are some best practices for managing IoT remote access?
10 best ssh clients for windows adalasopa
To connect to an IoT device, you need the device's IP address or hostname, the SSH port (default is 22), and the credentials (either a password or a private key). Best Practices for Secure SSH Access. Security is a top priority when remotely accessing IoT devices. Here are some best practices to ensure a secure SSH connection:
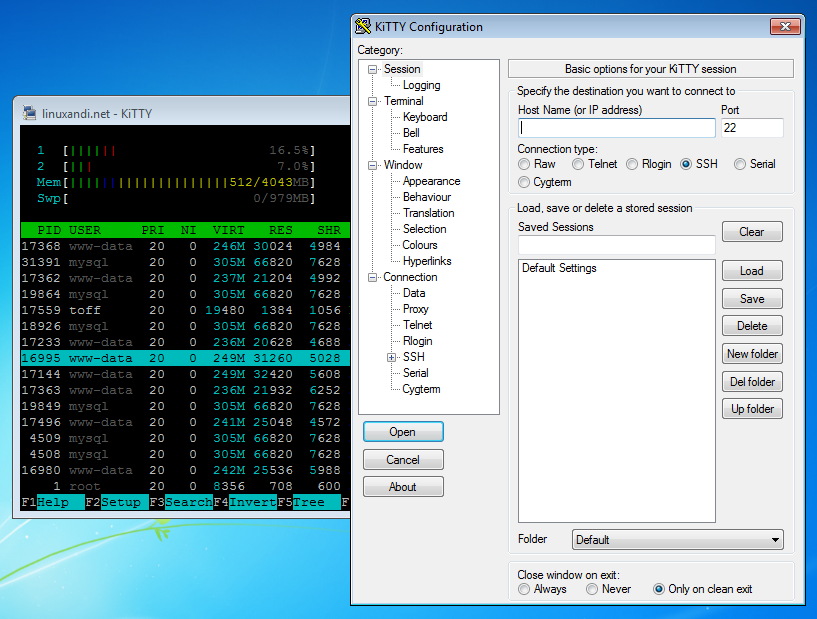
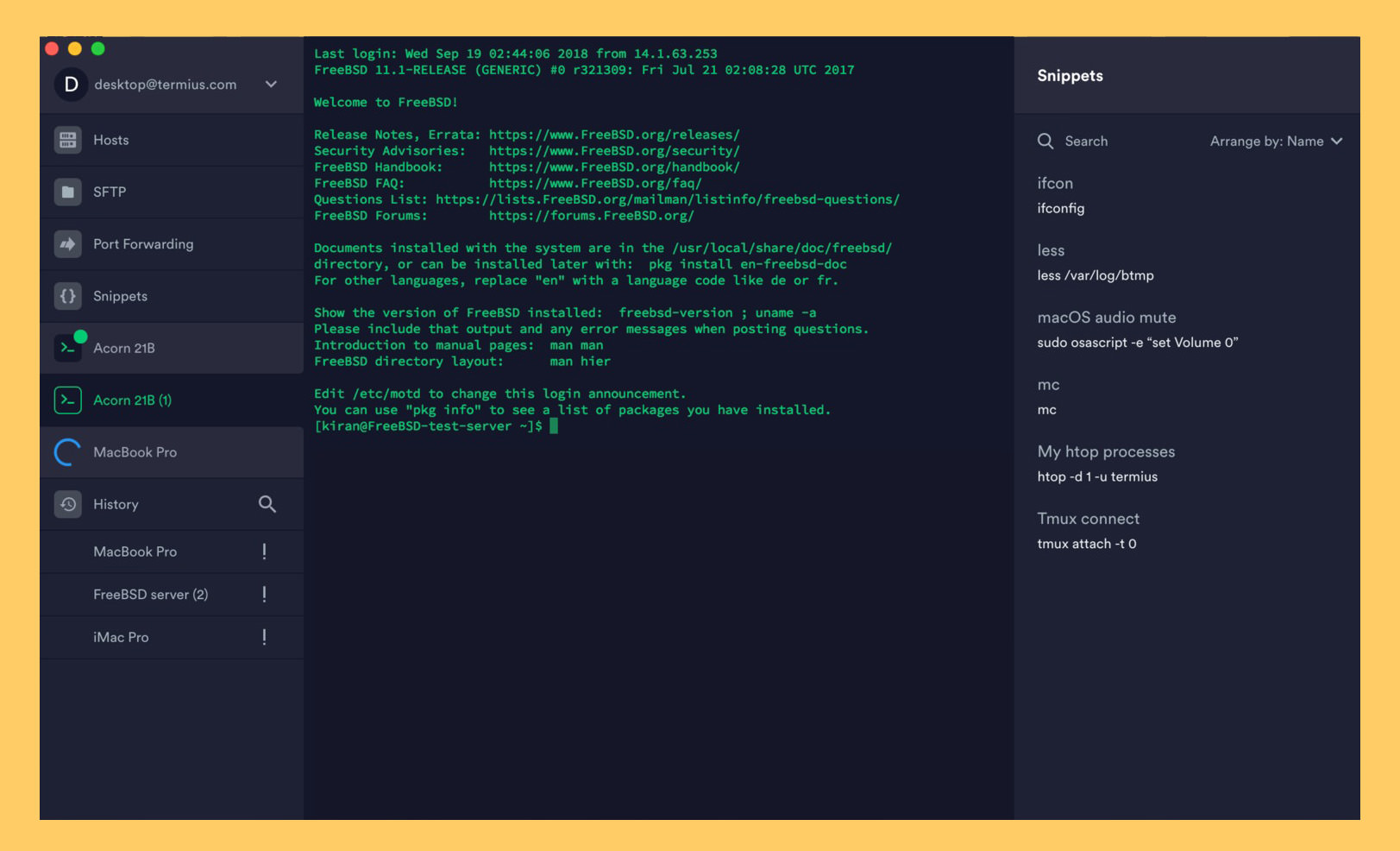
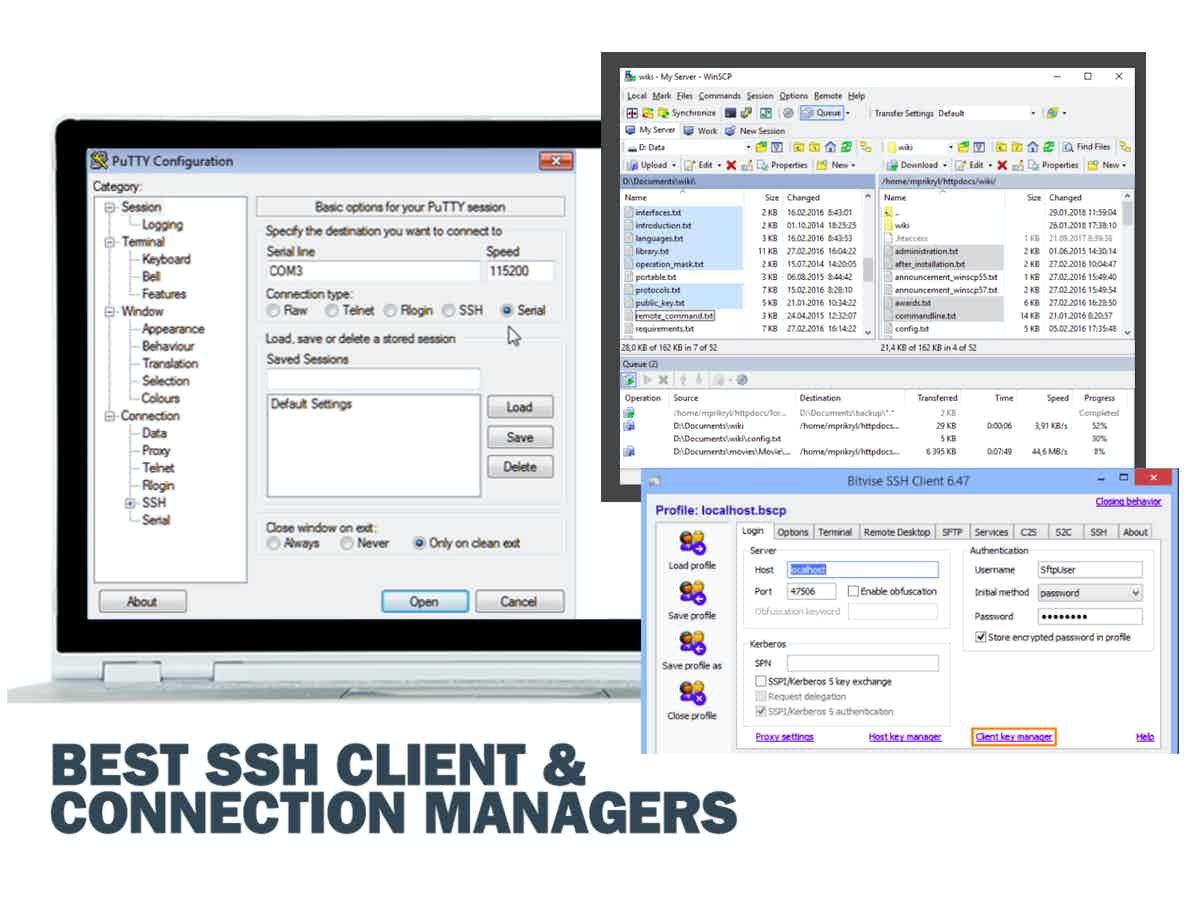
Top 17 Best SSH Clients for Windows & Linux
SSH is a cryptographic network protocol that allows secure remote access to devices over an unsecured network. In this article, we will discuss the benefits of using SSH for IoT security, best practices for implementing SSH, and how to access and manage IoT devices using SSH. The Benefits of Using SSH for IoT Security. SSH provides a secure and.

Ssh port forwarding for remote device access behind firewall Hackster.io
It enables you to establish an SSH connection to your devices from anywhere in the world. Step 1: Create a Tunnel to Your IoT Device. On your IoT device, open a terminal or SSH client and run the following command to create a tunnel to port 22 (SSH): ssh -p 443 -R0:localhost:22 [email protected]. This command establishes a secure connection to.

Top 25 IoT Devices Of All Time Software Testing Material
This article explores remote IoT device management, focusing on the secure ways to access Raspberry Pi web devices remotely. We will delve into two key methods - SSH (Secure Shell) and web-based access, highlighting the benefits they offer in overcoming firewall and network address translation challenges. One of the most trustworthy and secure.

Secure Remote Access to Your IoT Devices Tinkerman
Accessing the IoT device SSH from your laptop. Now you can access your IoT device's SSH server using the above SocketXP local endpoint, as shown below. $ ssh -i ~/.ssh/john-private.key john@localhost -p 3000. The above method uses SSH private key based authentication to SSH into your IoT device.
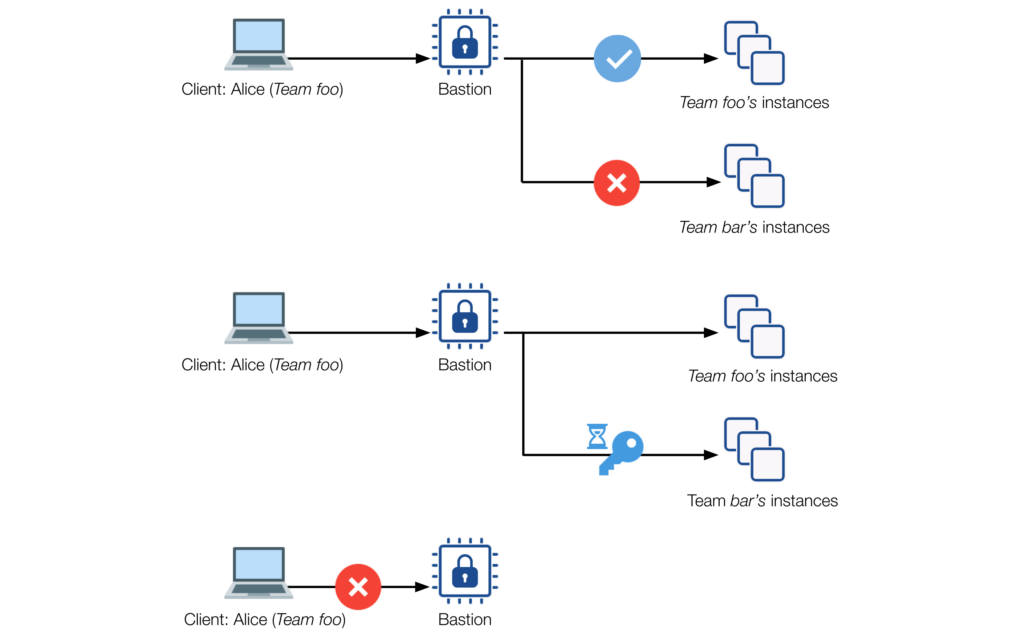
Flexible and Secure SSH access to cloud infrastructure — Part I Teads Engineering
Here are some security considerations to keep in mind when using SSH for remote access to your IoT device: Change the default SSH password: For example, a Raspberry Pi comes with a default username "pi" and password "raspberry" for SSH access. It is critical to change the default password to a strong and unique one as soon as possible.

System architecture for IoTbased smart home security. Download Scientific Diagram
It provides authentication and encryption, ensuring your commands and data remain confidential and protected from unauthorized access. The Benefits of Remote SSH IoT. When it comes to managing IoT devices, Remote SSH offers a plethora of advantages: Remote Access: Access and control your IoT devices from anywhere in the world.
Top Security Techniques to Protect of Things (IOT) Infrastructure
Step 1: Access your IoT device's terminal. Access the terminal of your IoT device, either through a direct connection or remotely. Getting into the terminal is like stepping into the brain of your IoT device. This is where you'll give all the commands to set up the SSH security. Step 2: Install an SSH server. Install an SSH server software.

Access IoT Devices from Anywhere Pinggy
Understanding SSH and Its Importance in IoT. SSH is a cryptographic network protocol that enables secure access to network services over an unsecured network. It is widely used for secure command-line access, remote execution of commands, and secure file transfers. In the context of IoT, SSH is crucial for managing devices, updating firmware.

Top 20 IoT Devices List You Must Know MindMajix
After you create a tunnel, you can either SSH within the browser or open a terminal outside the AWS IoT console to access your remote device. Thing details page. When you create the tunnel, you'll also be able to specify whether to use the most recent, open tunnel or create a new tunnel for the device, in addition to choosing the setup methods.
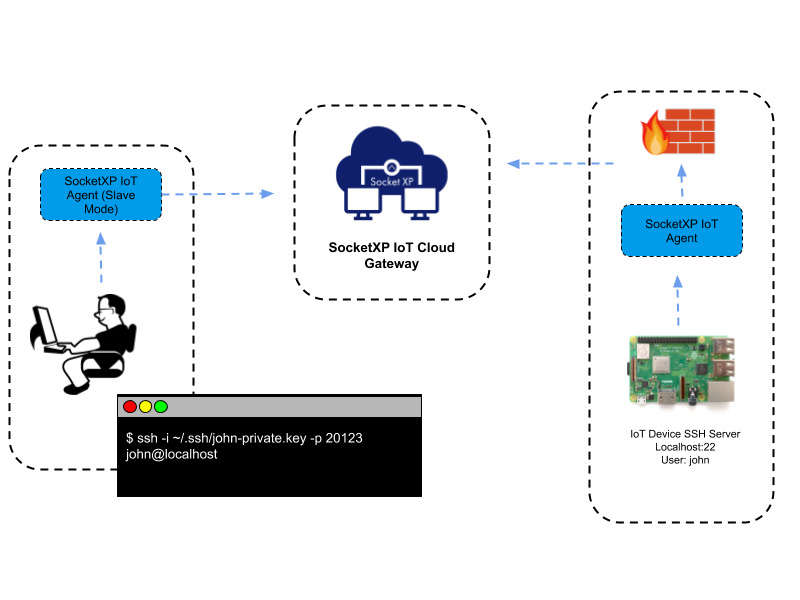
IoT Raspberry Pi SSH Remote Access over Starlink, 3G, 4G LTE, or 5G mobile cellular network by
Smart Retail: In smart retail applications, SSH is used for secure remote access and management of IoT devices such as inventory management systems, point-of-sale terminals, and digital signage. SSH ensures secure communication and control, preventing unauthorized access and protecting sensitive customer information. 8.
- Iglesia De San Juan Bautista
- Hoe Lang Blijft Rijden Onder Invloed Staan
- Hoe Laat Sluiten De Winkels In Amsterdam
- De Erfgenaam Gemist Aflevering 1
- Rössler Linie Gmbh Co Kg
- Wat Is De Engelse Term Voor Internetgebruiker
- Intocht Sinterklaas 2023 De Bilt
- Marcel En Ronald Auerbach Gestopt
- Bart Van Der Leck Kat
- Apollonia Van Ravenstein Mick Jagger
